Background: Fully Homomorphic Encryption Unveiled
Before we embark on our comparative analysis of the SEAL and OpenFHE libraries, let's unveil the revolutionary concept of Fully Homomorphic Encryption (FHE). In the realm of cryptography, FHE stands as a beacon of innovation, allowing computations on encrypted data without the need for decryption.
Traditional encryption methods ensure the confidentiality of sensitive information during transmission or storage. However, they often hinder the ability to perform computations on this encrypted data without decrypting it first. FHE, on the other hand, transcends these limitations by enabling operations directly on encrypted data, preserving its confidentiality throughout the computational process.
Introduction
In this technical blog, we delve into the world of FHE and conduct a comparative analysis of two leading open-source libraries: Microsoft SEAL and OpenFHE. Our exploration focuses on the implementation of two widely-used FHE schemes, Brakerski-Gentry-Vaikuntanathan (BGV) and Brakerski/Fan-Vercauteren.
Understanding OpenFHE and SEAL
OpenFHE: A Glimpse into Versatility
OpenFHE, powered by Duality Technologies, emerges as a versatile open-source homomorphic encryption library. Its popularity stems from its support for a diverse range of FHE schemes, including BFV, BGV, CKKS, FHEW, and TFHE. Additionally, OpenFHE incorporates multiparty extensions for threshold FHE and proxy re-encryption, providing a comprehensive toolkit for various cryptographic applications.
Explore OpenFHE: OpenFHE GitHub Repository
To download OpenFHE binaries, visit the OpenFHE GitHub Releases section.
SEAL: Harnessing Microsoft's Expertise
SEAL, an open-source library developed by Microsoft, is designed to implement the most popular FHE schemes in use today: BGV, BFV, and CKKS. Leveraging Microsoft's expertise in cryptography, SEAL offers a robust platform for secure computations over encrypted data.
Explore SEAL: SEAL GitHub Repository
To download SEAL binaries, visit the SEAL GitHub Releases section.
Homomorphic Operations Data and Analysis
For our comparative analysis, we leverage the resources available in the GitHub repository. The repository contains C programs and binaries, facilitating a more detailed and resourceful exploration.
The provided binaries include:
- SEAL BGV
- SEAL BFV
- OpenFHE BGV
- OpenFHE BFV
Each binary executes homomorphic addition and multiplication operations on encrypted data, producing runtime and result outputs. These binaries serve as the foundation for our exploration into the efficiency and performance of FHE schemes.
Data Generation and Analysis
To initiate our analysis, we generate at least ten unique combinations of inputs for both multiplication and addition operations, taken average over ten iterations. The resulting tables showcase the runtimes of these operations for each scheme within the SEAL and OpenFHE libraries.
Pre-compiled binaries for the above libraries are provided at GitHub repository. To build you own binaries refer appendix. One can runs the binaries as follows.
./openFHE_BFV 1 1 2
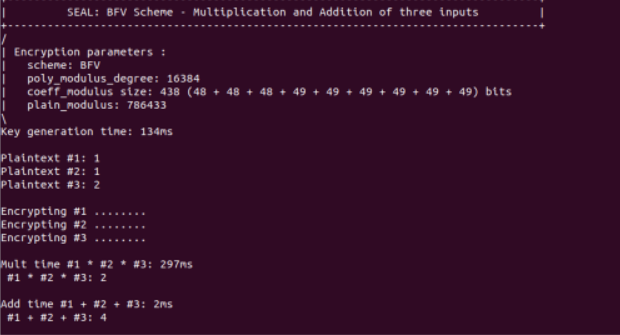
Multiplication:
| Input1 | Input2 | Input3 | OpenFHE_BFV | OpenFHE_BGV | SEAL_BFV | SEAL_BGV |
|---|---|---|---|---|---|---|
| 1 | 2 | 3 | 52 | 26 | 118 | 43 |
| 4 | 5 | 6 | 54 | 26 | 115 | 47 |
| 7 | 8 | 9 | 55 | 28 | 118 | 44 |
| 10 | 11 | 12 | 56 | 29 | 121 | 46 |
| 13 | 14 | 15 | 56 | 26 | 124 | 44 |
| 16 | 17 | 18 | 58 | 28 | 120 | 50 |
| 19 | 20 | 21 | 57 | 28 | 114 | 48 |
| 22 | 23 | 24 | 52 | 28 | 120 | 46 |
| 25 | 26 | 27 | 55 | 28 | 121 | 45 |
| 28 | 29 | 30 | 56 | 28 | 120 | 45 |
Visualization for Enhanced Comprehension
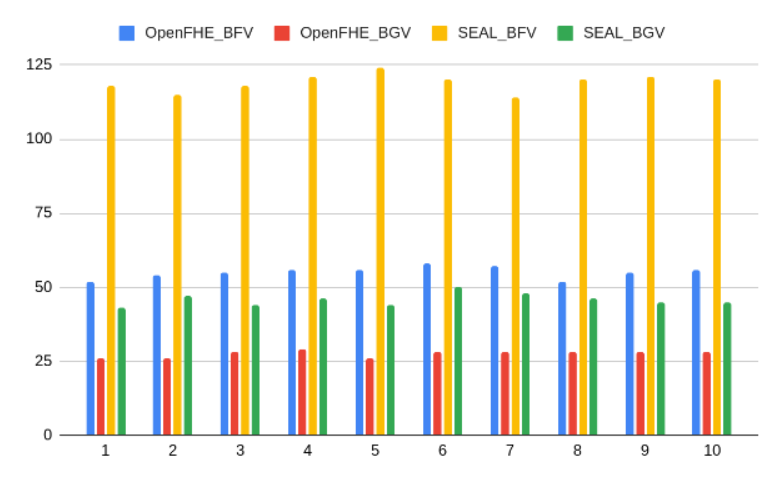
Addition:
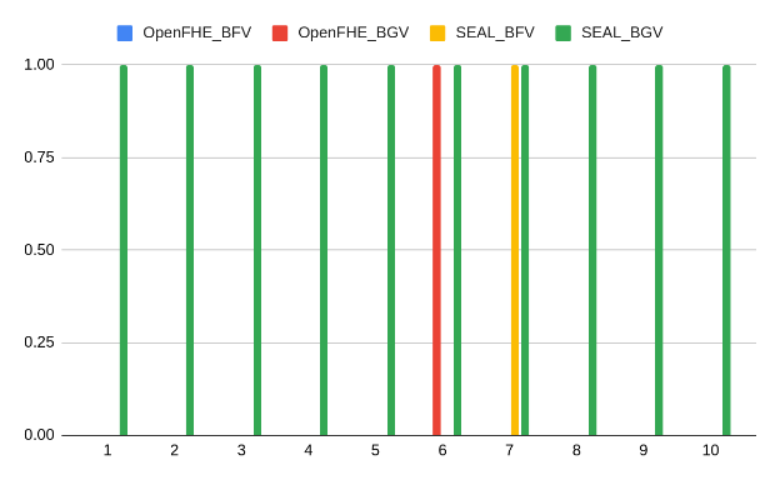
| Input1 | Input2 | Input3 | OpenFHE_BFV | OpenFHE_BGV | SEAL_BFV | SEAL_BGV |
|---|---|---|---|---|---|---|
| 1 | 2 | 3 | 0 | 0 | 0 | 1 |
| 4 | 5 | 6 | 0 | 0 | 0 | 1 |
| 7 | 8 | 9 | 0 | 0 | 0 | 1 |
| 10 | 11 | 12 | 0 | 0 | 0 | 1 |
| 13 | 14 | 15 | 0 | 0 | 0 | 1 |
| 16 | 17 | 18 | 0 | 1 | 0 | 1 |
| 19 | 20 | 21 | 0 | 0 | 1 | 1 |
| 22 | 23 | 24 | 0 | 0 | 0 | 1 |
| 25 | 26 | 27 | 0 | 0 | 0 | 1 |
| 28 | 29 | 30 | 0 | 0 | 0 | 1 |
Visualization for Enhanced Comprehension
Comparing the overheads when FHE is not used
The GitHub repository also includes C programs that perform identical multiplication and addition operations on 64-bit integer values. The execution times are compared with FHE operations, revealing the overheads associated with FHE execution.
#include <stdio.h>
#include <stdlib.h>
#include <time.h>
#include <inttypes.h>
int main(int argc, char *argv[]) {
int64_t num1, num2, num3;
if (argc >= 4) {
num1 = strtoll(argv[1], NULL, 10);
num2 = strtoll(argv[2], NULL, 10);
num3 = strtoll(argv[3], NULL, 10);
} else {
printf("usage: ./c_program <num1> <num2> <num3> \n");
return 1;
}
int64_t add, mul;
clock_t start, end;
double add_time, mul_time;
start = clock();
add = num1 + num2 + num3;
end = clock();
add_time = ((double) (end - start)) / CLOCKS_PER_SEC * 1000; //time in milliseconds.
// Perform multiplication
start = clock();
mul = num1 * num2 * num3;
end = clock();
mul_time = ((double) (end - start)) / CLOCKS_PER_SEC * 1000; //time in milliseconds
// Output results
printf("mul_time: %lf add_time%lf\n", mul_time, add_time);
return 0;
}
Multiplication:
| Input1 | Input2 | Input3 | non_FHE | OpenFHE_BFV | OpenFHE_BGV | SEAL_BFV | SEAL_BGV |
|---|---|---|---|---|---|---|---|
| 1 | 2 | 3 | 0.0009 | 52 | 26 | 118 | 43 |
| 4 | 5 | 6 | 0.001 | 54 | 26 | 115 | 47 |
| 7 | 8 | 9 | 0.001 | 55 | 28 | 118 | 44 |
| 10 | 11 | 12 | 0.0009 | 56 | 29 | 121 | 46 |
| 13 | 14 | 15 | 0.001 | 56 | 26 | 124 | 44 |
| 16 | 17 | 18 | 0.0017 | 58 | 28 | 120 | 50 |
| 19 | 20 | 21 | 0.0005 | 57 | 28 | 114 | 48 |
| 22 | 23 | 24 | 0.0003 | 52 | 28 | 120 | 46 |
| 25 | 26 | 27 | 0.0006 | 55 | 28 | 121 | 45 |
| 28 | 29 | 30 | 0.0011 | 56 | 28 | 120 | 45 |
Average Overheads:
| Overheads (ms) | non-FHE | OpenFHE_BFV | OpenFHE_BGV | SEAL_BFV | SEAL_BGV |
|---|---|---|---|---|---|
| Multiplication | 0.0009 | 55.0991 | 27.4991 | 119.0991 | 45.7991 |
Addition:
| Input1 | Input2 | Input3 | non_FHE | OpenFHE_BFV | OpenFHE_BGV | SEAL_BFV | SEAL_BGV |
|---|---|---|---|---|---|---|---|
| 1 | 2 | 3 | 0.0014 | 0 | 0 | 0 | 1 |
| 4 | 5 | 6 | 0.0017 | 0 | 0 | 0 | 1 |
| 7 | 8 | 9 | 0.001 | 0 | 0 | 0 | 1 |
| 10 | 11 | 12 | 0.0012 | 0 | 0 | 0 | 1 |
| 13 | 14 | 15 | 0.001 | 0 | 0 | 0 | 1 |
| 16 | 17 | 18 | 0.009 | 0 | 1 | 0 | 1 |
| 19 | 20 | 21 | 0.0009 | 0 | 0 | 1 | 1 |
| 22 | 23 | 24 | 0.0008 | 0 | 0 | 0 | 1 |
| 25 | 26 | 27 | 0.0008 | 0 | 0 | 0 | 1 |
| 28 | 29 | 30 | 0.0014 | 0 | 0 | 0 | 1 |
Average Overheads:
| Overheads (ms) | non-FHE | OpenFHE_BFV | OpenFHE_BGV | SEAL_BFV | SEAL_BGV |
|---|---|---|---|---|---|
| Addition | 0.00192 | 0.00192 | 0 | 0.1 | 0.1 |
Conclusion
Our analysis brings forth a compelling narrative. OpenFHE demonstrates superior implementation of FHE schemes, with OpenFHE_BGV emerging as the top performer, closely followed by OpenFHE_BFV. SEAL, while robust, exhibits higher runtimes compared to OpenFHE, suggesting that OpenFHE's implementation is more efficient.
Explore Further
To delve deeper into the world of homomorphic encryption and contribute to its advancements, consider exploring the GitHub repositories for OpenFHE and SEAL:
- Explore OpenFHE: OpenFHE GitHub Repository
- Explore SEAL: SEAL GitHub Repository
Download the respective binaries from the library repositories and engage in the evolving landscape of homomorphic encryption.
This exploration not only enhances our understanding of FHE but also contributes valuable insights to the ongoing development of secure and privacy-preserving computational technologies.
Appendix
This section provides details on the build process for two libraries. The instructions are presented to facilitate independent experimentation with Fully Homomorphic Encryption (FHE) implementations.
Prerequisites
To execute this project, ensure that the following dependencies are installed:
- CMake
- G++
- GMP
- Clang
OpenFHE
Navigate to the openfhe directory and follow these steps to set up the project:
mkdir build
cd build
cmake ..
make
make install
make testall
After modifying the code, compile test programs using the following commands:
make added_bgv
make added_bfv
To execute the examples, run the binaries as follows:
bin/examples/pke/added_bgv
bin/examples/pke/added_bfv
Additionally, new files created will be automatically linked during the make process.
SEAL
Set up this library with the following instructions:
cmake -S . -B build -DSEAL_BUILD_EXAMPLES=ON
cmake --build build
sudo cmake --install build
To run the compiled work, locate the binary at build/bin/sealexamples.
